卡巴斯基報告:能源和工控系統(tǒng)集成公司面臨最高的網絡攻擊風險
http://www.debgrams.com 2018-04-10 16:45 《中華工控網》翻譯
Kaspersky Report: Energy and ICS Integration companies face highest chance of cyberattack
卡巴斯基報告:能源和工控系統(tǒng)集成公司面臨最高的網絡攻擊風險
A report from Kaspersky Lab found that in the second half of 2017, nearly 40 percent of all industrial control systems (ICS) in energy organizations protected by Kaspersky Lab solutions were attacked by malware at least once – closely followed by 35 percent of engineering & ICS integration networks.
卡巴斯基實驗室發(fā)布的一份報告發(fā)現(xiàn),在2017年下半年,受卡巴斯基實驗室解決方案保護的能源組織中,有近40%的工業(yè)控制系統(tǒng)(ICS)至少遭到一次的惡意軟件攻擊,緊隨其后的是35%的工程和工控系統(tǒng)集成網絡。
The Kaspersky Lab report, “Threat Landscape for Industrial Automation Systems in H2 2017,” also found that for all other industries (manufacturing, transportation, utilities, food, healthcare, etc.) the proportion of ICS computers attacked ranged from 26 percent to 30 percent on average. The vast majority of detected attacks were accidental hits.
這份“2017年下半年工業(yè)自動化系統(tǒng)威脅情況”卡巴斯基實驗室報告還發(fā)現(xiàn),對于所有其他行業(yè)(制造業(yè)、交通運輸業(yè)、公用事業(yè)、食品、醫(yī)療保健等)而言,工控系統(tǒng)計算機遭受攻擊的比例平均介乎26%到30%之間。絕大多數(shù)檢測到的攻擊都是意外擊中。
The cybersecurity of industrial facilities remains an issue that can lead to very serious consequences affecting industrial processes, as well as businesses losses. While analyzing the threat landscape in different industries, Kaspersky Lab ICS CERT recorded that nearly all industries regularly experience cyberattacks on their ICS computers. However, there are two industries that were attacked more than others – energy organizations (39%), and engineering and ICS integration businesses (35%).
工業(yè)設施的網絡安全仍然是一大問題,可能導致影響工業(yè)流程的嚴重后果,造成企業(yè)損失。在分析不同行業(yè)的威脅情況時,卡巴斯基實驗室工控系統(tǒng)網絡應急響應小組記錄了幾乎所有行業(yè)其工控系統(tǒng)計算機日常遭受的網絡攻擊。但有兩個行業(yè)較其他行業(yè)受到的攻擊更多,那就是能源機構(39%),以及工程和工控系統(tǒng)集成業(yè)務(35%)。
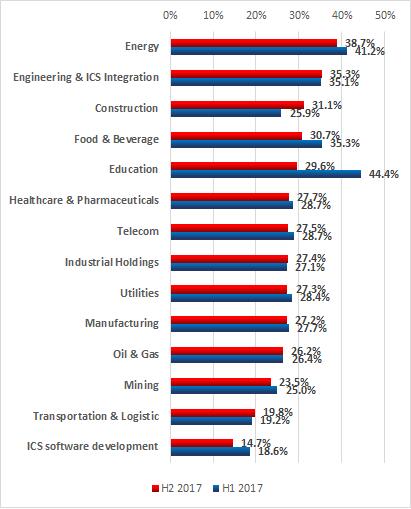
The sector that demonstrated the most noticeable growth of ICS computers attacked during the second half of 2017 (compared to the first half of 2017) was construction, with 31 percent attacked. The relatively high percentage of attacked ICS computers in the construction industry compared to the first half of 2017 could indicate that these organizations are not necessarily mature enough to pay the required attention to the protection of industrial computers. Their computerized automation systems might be relatively new and an industrial cybersecurity culture is still being developed in these organizations.
在2017年下半年(與2017年上半年相比),工控系統(tǒng)計算機受攻擊上升最為明顯的行業(yè)是建筑業(yè),有31%受到攻擊。與2017年上半年相比,建筑行業(yè)受到攻擊的工控系統(tǒng)計算機的比例相對較高,這可能表明這些機構未必足夠成熟,無法對工業(yè)計算機的保護給予必要的關注。他們的計算機自動化系統(tǒng)可能相對較新,并且這些組織仍未確立工業(yè)網絡安全意識。
The lowest percentage of ICS attacks – 15 percent – has been found in enterprises specializing in developing ICS software, meaning that their ICS research/development laboratories, testing platforms, demo stands and training environment are also being attacked by malicious software, although not as often as the ICS computers of industrial enterprises. Kaspersky Lab ICS CERT experts point to the significance of ICS vendors’ security, because the consequences of an attack spreading over the vendor’s partner ecosystem and customer base could be very dramatic – as seen during the ExPetr malware epidemic.
專注于開發(fā)工控系統(tǒng)軟件的企業(yè)受攻擊比例最低,僅為15% ,不過這意味著這些工控系統(tǒng)研究/開發(fā)實驗室、測試平臺、演示臺和培訓環(huán)境也會受到惡意軟件的攻擊,盡管不像工業(yè)企業(yè)的工控系統(tǒng)計算機那么頻繁。卡巴斯基實驗室工控系統(tǒng)網絡應急響應小組專家了指出工控系統(tǒng)供應商安全的重要性,因為對供應商合作伙伴生態(tài)系統(tǒng)和客戶群的攻擊蔓延的后果可能非常強烈——正如ExPetr惡意軟件流行期間所發(fā)生的。
Among the new trends of 2017, Kaspersky Lab ICS CERT researchers have discovered a rise in mining attacks on ICS. This growth trend began in September 2017, along with an increase in the cryptocurrency market and miners in general. But in the case of industrial enterprises, this type of attack can pose a greater threat by creating a significant load on computers, and as a result, negatively affecting the operation of the enterprise’s ICS components and threatening their stability.
在2017年的新趨勢中,卡巴斯基實驗室工控系統(tǒng)網絡應急響應小組的研究人員發(fā)現(xiàn)了對工控系統(tǒng)挖礦攻擊的增加。這種增長趨勢始于2017年9月,伴隨加密貨幣市場火爆和礦工總體增加。但對工業(yè)企業(yè)而言,這類攻擊可能會對計算機造成重大負擔從而構成更大的威脅,對企業(yè)的工控系統(tǒng)組件的運行產生負面影響并威脅其穩(wěn)定性。
Overall, during the period from February 2017 to January 2018, cryptocurrency mining programs attacked three percent of industrial automation system computers, in most cases accidentally.
總的來說,在2017年2月至2018年1月期間,加密電子貨幣挖掘程序攻擊了3%的工業(yè)自動化系統(tǒng)計算機,絕大多數(shù)是意外攻擊。
Other highlights from the report include:
報告的其他亮點包括:
- Kaspersky Lab products blocked attempted infections on 38% of ICS computers protected by them. This is 1.4 percentage points less than in the second half of 2016.
- The internet remains the main source of infection with 22.7% of ICS computers attacked. This is two percent higher than in the first six months of the year. The percentage of blocked web-borne attacks in Europe and North America is substantially lower than elsewhere.
- The top five countries by percentage of ICS computers attacked has remained unchanged since reported in the first half of 2017. This includes Vietnam (70%), Algeria (66%), Morocco (60%), Indonesia (60%) and China (60%).
- In the second half of 2017, the number of different malware modifications detected by Kaspersky Lab solutions installed on industrial automation systems increased from 18,000 to over 18,900.
- In 2017, 11% of all ICS systems were attacked by botnet agents, a malware that secretly infects machines and includes them in a botnet network for remote command execution; the main sources of attacks like this were the internet, removable media and email messages.
- In 2017, Kaspersky Lab ICS CERT identified 63 vulnerabilities in industrial systems and IIoT/IoT systems, and 26 of them have been fixed by vendors.
- 有38%的受卡巴斯基實驗室產品保護的工控系統(tǒng)計算機遭遇攻擊,比2016年下半年減少1.4個百分點。
- 互聯(lián)網仍然是主要感染源,有22.7%的工控系統(tǒng)計算機遭受攻擊,比當年前六個月高出兩個百分點。歐洲和北美網絡攻擊受阻的比例明顯低于其他地區(qū)。
- 自2017年上半年報告以來,工控系統(tǒng)計算機遭受攻擊的前五位國家百分比保持不變。其中包括越南(70%),阿爾及利亞(66%),摩洛哥(60%),印度尼西亞(60%)和中國( 60%)。
- 在2017年下半年,安裝在工業(yè)自動化系統(tǒng)上的卡巴斯基實驗室解決方案檢測到的不同惡意軟件修改數(shù)量從18,000個增加到18,900個以上。
- 2017年,所有工控系統(tǒng)中有11%受到僵尸網絡代理的攻擊,這是一種惡意軟件,它會秘密感染機器并將其包含在僵尸網絡中以執(zhí)行遠程命令,這種攻擊的主要來源是互聯(lián)網、可移動媒介和電子郵件。
- 2017年,卡巴斯基實驗室工控系統(tǒng)網絡應急響應小組發(fā)現(xiàn)了工業(yè)系統(tǒng)和工業(yè)物聯(lián)網 / 物聯(lián)網系統(tǒng)中的63個漏洞,其中26個已被供應商修復。
“The results of our research into attacked ICS computers in various industries have surprised us, “said Evgeny Goncharov, head of Kaspersky Lab ICS CERT. “For example, the high percentage of ICS computers attacked in power and energy companies demonstrated that the enterprises’ effort to ensure cybersecurity of their automation systems after some serious incidents in the industry is not enough, and there are multiple loopholes still there that cybercriminals can use.”
卡巴斯基實驗室工控系統(tǒng)網絡應急響應小組負責人Evgeny Goncharov表示:“我們對各行業(yè)受攻擊工控系統(tǒng)計算機的研究結果讓我們感到驚訝。例如,電力和能源公司遭受工控系統(tǒng)計算機攻擊的比例很高,這表明企業(yè)在行業(yè)發(fā)生嚴重事故后確保其自動化系統(tǒng)網絡安全的努力是不夠的,留給網絡犯罪分子利用的漏洞仍然很多。”
Kaspersky Lab ICS CERT recommends the following technical measures to be taken:
卡巴斯基實驗室工控系統(tǒng)網絡應急響應小組建議采取以下技術措施:
- Regularly update operating systems, application software and security solutions on systems that are part of the enterprise’s industrial network.
- Restrict network traffic on ports and protocols used on the edge routers and inside organization's OT networks.
- Audit ICS component access control in the enterprise’s industrial network and at its boundaries.
- Deploy dedicated endpoint protection solutions onto ICS servers, workstations and HMIs to secure OT and industrial infrastructure from random cyberattacks.
- Deploy network traffic monitoring, analysis and detection solutions for better protection from targeted attacks.
- 定期更新企業(yè)工業(yè)網絡系統(tǒng)中的的操作系統(tǒng)、應用軟件和安全方案。
- 限制邊緣路由器和企業(yè)運營網絡內使用的端口和協(xié)議的網絡流量。
- 在企業(yè)工業(yè)網絡及其邊界內,審核工控系統(tǒng)組件訪問控制。
- 將專用端點保護解決方案部署到工控系統(tǒng)服務器、工作站和人機界面上,以保護運營和工業(yè)基礎設施免受隨機網絡攻擊。
- 部署網絡流量監(jiān)控、分析和檢測解決方案,以更好地防范有針對性的攻擊。
相關新聞
- ? 工業(yè)安全傳感器市場強勢復蘇,國產“黑馬”突圍破局!
- ? 涉及重要工業(yè)產品質量安全,市場監(jiān)管總局公開征求意見
- ? 麥德勝智能測控創(chuàng)新中心啟用,開啟工業(yè)安全綠色發(fā)展新紀元
- ? GS1標準助力重點工業(yè)產品質量安全追溯系統(tǒng)建設
- ? 皮爾磁:定制化的權限控制使管理如此清晰
- ? 中控技術多款網絡安全產品入選《工業(yè)控制系統(tǒng)信息安全產品及服務指南(2024版)》
- ? 2024北京安博會 | 佰維存儲:深諳工業(yè)級應用特性,驅動智能安防新未來
- ? 2024 SGS工業(yè)功能安全及OT安全技術論壇成功舉辦
- ? 海康威視發(fā)布機械臂防碰撞相機,助力生產安全場景數(shù)字化
- ? 皮爾磁:PSENslock2榮獲工業(yè)安全類最佳產品獎
編輯精選
- ? 賦能綠色智造 臺達與長三角制造企業(yè)探討智造新路徑
- ? 2025 年伺服電機行業(yè)產業(yè)布局深度解析
- ? HMS行業(yè)洞察:2025工業(yè)網絡市場全景解讀
- ? 總投資15億元!ABB超級工廠落子南京
- ? 構筑工業(yè) AI 時代的數(shù)據(jù)底座,藍卓supOS X工廠操作系統(tǒng)全球首發(fā)
- ? CC-Link協(xié)議家族與會員單位集中亮相,共話行業(yè)新發(fā)展
- ? 2025 工業(yè)操作系統(tǒng)大會在蘇州隆重開幕
- ? 創(chuàng)新、落地、增效:施耐德電氣以AI賦能產業(yè)新生態(tài)
- ? 西門子2026 年數(shù)字化程度展望
- ? 國家統(tǒng)計局:11月工業(yè)機器人產量增長超20%
工控原創(chuàng)
- ? 統(tǒng)一以太網標準再迎里程碑,SPE 和 Ethernet-APL 解鎖工業(yè)數(shù)字化新機遇
- ? 11月RatingDog中國制造業(yè)PMI降至49.9,供需走弱重回收縮區(qū)間
- ? 11月工控圈發(fā)生了這些矚目的大事件
- ? 十月工控領域重要資訊,一睹為快!
- ? 回顧 | 以技術干貨 + 落地案例,解鎖產業(yè)升級新路徑
- ? ABB報告:工業(yè)停機每小時損失高達50萬美元,知行鴻溝阻礙現(xiàn)代化更新
- ? ABB宣布以53.75億美元將機器人業(yè)務出售給軟銀
- ? 九月不容錯過的工控圈大事
- ? 當“軟件定義”與“價值鏈”相遇,未來工業(yè)走向何方?
- ? 西門子:以“一次正確”破局內卷,讓工業(yè)AI真正落地




